In the wake of burgeoning cyber threats, the Zero Trust security model has surged in adoption since 2019. This model, defined by a “never trust, always verify and enforce least privilege” doctrine, applies rigorous scrutiny to both internal and external network access. Whether traffic is coming from within or outside the organization, it all undergoes the same level of meticulous inspection and logging.
However, while Zero Trust has become an industry buzzword, it is not without its limitations, such as:
- Potential network bottlenecks caused by overly strict access controls or slow verification processes.
- Lack of focus on network issues like DDoS attacks, human errors, and poorly configured devices.
- Inefficiencies in CPU-intensive operations, especially when using traditional Next-Generation Firewalls (NGFW) for encrypted traffic inspection.
The Quest for a Robust Hardware Solution
One of our valued clients sought a robust hardware appliance to run a proprietary security solution tailored to both business and security needs. This led us to develop an offering that would overcome traditional pain points and provide:
- Network Access Control: Identifying, tracking, and managing device roles and network privileges.
- Internal Segmentation Firewalls (ISFWs): Surpassing the limitations of traditional NGFWs.
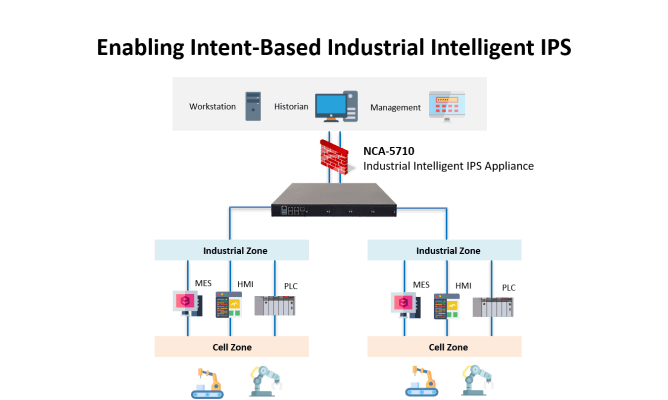
- Intent-Based Segmentation: Translating business and security requirements into functional network segmentation policies without causing bottlenecks.
Unveiling the L-5710: A Powerhouse in Network Security Hardware
Our L-5710, engineered with the 2nd Gen Intel® Xeon® Processor Scalable Family, is a high-performance hardware solution. It boasts dual CPU computing power and virtualization capabilities in a 19” 1U form factor, but that’s not all. Features like Intel® QuickAssist Technology, Intel® AVX-512 instructions, Intel® Hyperscan, and Data Plane Development Kit (DPDK) further amplify its efficiency.
Key Specifications:
- Memory: Up to 384GB DDR4 system memory at 2666 MHz.
- Networking: Options for either 4x GbE RJ-45 or 4x 10G SFP+ ports.
- Expandability: 4x NIC module slots, supporting 10G/25G/40G/100G fiber/copper/bypass specs.
Multi-Faceted Benefits of the L-5710
When deployed for advanced internal segmentation and intrusion prevention, the L-5710 offers several advantages:
- Ease of Integration and Management: Industry-standard design simplifies deployment and maintenance.
- Adaptive Network Protection: Provides real-time, continuous threat protection through a centralized interface.
- Enhanced Visibility and Reliability: High-level asset tracking and robust IT/OT communication.
- 24/7 Operational Capability: Designed for continuous operation, thanks to features like hardware bypass and redundant power supplies.
Demonstrable Results: A Case Study
Implementing the L-5710 allowed our client to successfully deploy a network architecture that provided comprehensive ICS network security, reduced the impact of cyber incidents, and facilitated easy management. Our hardware solution fit seamlessly into their IT-OT convergency network environment, empowering them to handle micro-segmentation and cybersecurity challenges, even in complex settings.
Conclusion: The L-5710 as the Ultimate Enabler for Zero Trust Security
In a world where the Zero Trust model is increasingly becoming the new normal, our L-5710 stands as a purpose-built hardware solution that tackles the limitations and amplifies the benefits. This is not just another appliance; it’s a cornerstone for modern network security architecture, designed to bring out the best in your proprietary software solutions.
Ready to future-proof your network security with a hardware solution designed for the challenges of the modern digital landscape? Don’t compromise when it comes to protecting your enterprise. Contact us today to learn how the L-5710 can be the cornerstone of your Zero Trust security strategy.